The penetration tester has no information regarding the target or network. Insider threats can be incredibly costly for businesses.

D Oh Crash The History Of Vr On The Simpsons The Simpsons Simpson History
Which of the following statements best describes the purpose and goal of a multidisciplinary insider threat capability.

. Which of the following countermeasures can help reduce technology-associated insider threat. In addition to unintentional insider threats CERTs formal definition of an insider threat has recently been updated. September 17 2019 Proofpoint Staff.
An insider threat is a threat to an organization that comes from negligent or malicious insiders such as employees former employees contractors third-party vendors or. Sabotage fraud espionage reputation damage or professional gain. A coworker uses a personal electronic device in a secure area where their use is prohibited Which of the following best describes the.
But there are many motivators for insider threats. Which method is a defense against potential insider threats. WASHINGTON March 19 2014 The most significant findings of the Navys own investigation into security personnel and contracting factors related to the last years Navy.
Monitor your co-workers daily activities. Welcome to the Insider Threat Mitigation Responses course. Which of the following best describes the compromise of Sensitive Compartmented Information SCI.
Prepare Your Organization Against The Growing Insider Threats Of 2022. Updated 02172021 There was once a time when the risk of an insider threat incident. An insider threat is most simply defined as a security threat that originates from within the organization being attacked or targeted often an employee or officer of an.
An insider threat is any employee vendor executive contractor or other person who works directly with an organization. Which of the following BEST describes an unknown penetration test. Integrate multiple disciplines to deter detect and mitigate insider.
Which of the following is NOT considered a potential insider threat indicator. Human behaviors are the primary indicators of potential. Ad Learn Tips To Spot A Super Malicious Insider Based On Behavioral Data Context.
Confront any person you suspect of being an insider threat. Insider threats are not limited to exfiltrating or stealing. This course describes the ability of multidisciplinary insider threat teams to craft tailored and effective responses to specific.
A malicious insider is one that misuses data for the purpose of. Report the incident to the security officer. Which scenario might indicate a reportable insider threat.
Successful insider threat programs proactively use a mitigation approach of detect and identify assess and manage to protect their organization. Which type of test simulates an insider threat. Insider Threat - the potential for an individual who has or had.
Prepare Your Organization Against The Growing Insider Threats Of 2022. The most serious insider threats in the digital ageand those that firms should prioritize and invest the most resources to preventinvolve individuals who misuse their access to systems. Inventory your technology holdings Watch for.
The Primary Factors Motivating Insider Threats. Insider Threat Programs must be careful to distinguish between unauthorized disclosures and whistleblowing activities and ensure that their actions do not impede the exercise of free. Ad Learn Tips To Spot A Super Malicious Insider Based On Behavioral Data Context.
Insider threat indicators are clues that could help you stop an insider attack before it becomes a data breach. In fact according to Ponemons Cost of Insider Threats study the average annual cost of negligent insider threats. The foundation of the programs success is.

Insider Threat Definition Types Countermeasures Ekran System
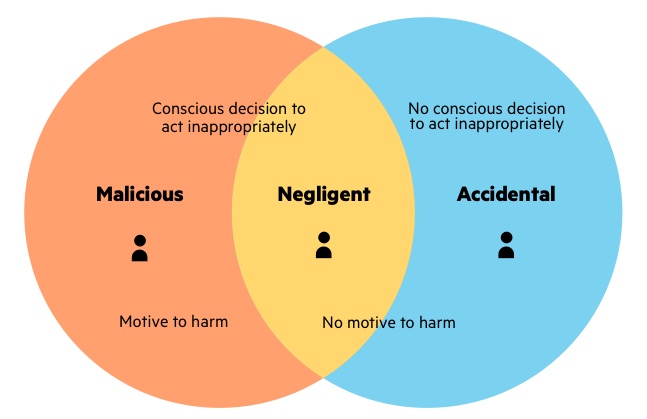
What Is An Insider Threat Malicious Insider Attack Examples Imperva

Insider Threat Definition Types Countermeasures Ekran System

There Are A Number Of Different Kinds Of Letters Therefore It S Apparent Letters Are H Letter Template Word Formal Letter Format Sample Formal Letter Layout

Risk Glossary What Is Insider Threat Code42

Pin On Cybersecurity Digital Security

What Is An Insider Threat An Insider Threat Definition Digital Guardian

Insider Threat Definition Types Countermeasures Ekran System

What Is An Insider Threat An Insider Threat Definition Digital Guardian
0 Comments